What is Malware?
Simply put, malware is malicious software—”any program or file that is intentionally harmful to a computer, network, or server.” Cyber criminals can implant malware onto your devices or into your network through cloud access or even emailing a file. It can be...
Why You Need a Password Manager
We’re sorry to be the bearers of bad news, but your “luckykitty92” password from middle school is a lot easier to crack than you’d like to believe. But, we also know that long and strong passwords are difficult to remember. Enter: password managers! These tools help...
What is Data Exfiltration?
As a business, the data you keep safe is probably your most important asset and possession, aside from your clients or customers. So what happens when cyber criminals get ahold of that data? Or if an employee leaves the company and takes any sensitive data they have...
Everything You Need to Know About Cookies
Unfortunately, cookies are not just a sweet treat to enjoy with milk. They also exist in technology! We’re sure you’ve seen a little pop up on websites that says something along the lines of: “This website uses cookies” with accept, decline, and manage buttons. Most...
How to Spot and Avoid Phishing Scams
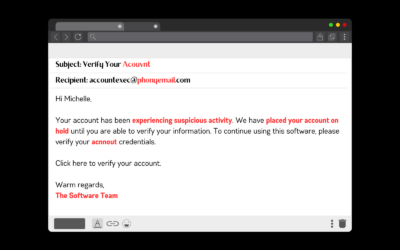
Phishing—not fishing—is a common cybersecurity scam. It’s relatively easy to fall prey to these scams, and they can be hard to detect. So it’s important to know what phishing scams are, common things to look out for, and how to protect yourself from them. Let’s get...
What is Multi-Factor Authentication?
In our digital world, keeping your information secure should be a top priority. One way to do that is through multi-factor authentication (MFA). Simply put, multi-factor authentication (sometimes called two-factor authentication) is the process of verifying your...
How to Stay Secure as Someone Who Works from Home
In the world of AI, remote work, and digital everything, it’s more important than ever to stay secure. But working at home, you don’t have the power of an in-house IT team (unless you work in IT, obviously)...so here are a few tips to stay cyber-secure when you work...
Cybersecurity Training is Important for Any Team, Not Just the Experts
Job security for cybersecurity experts seems to be airtight for the foreseeable future. According to Cybercrime Magazine: Cybercrime is expected to exceed $10 trillion annually by 2025 (up from $3 trillion in 2015) The average cost of a data breach last year was 4.35...
5 Common IT Problems to Avoid with the Right IT Support
It’s easy for an organization to bury its head in the figurative sand when it comes to technology issues and IT maintenance. This is something that leading IT support providers and cybersecurity experts see time and time again. Some organizations might lack a...
Maximizing ROI: Managed IT Services Provider vs. Internal IT Team
As IT infrastructure continues to be a key focus for businesses, the choice between handling IT internally or opting for a managed IT services provider is a pivotal one, influencing the efficiency, security and overall success of an organization. For many...