Phishing—not fishing—is a common cybersecurity scam. It’s relatively easy to fall prey to these scams, and they can be hard to detect. So it’s important to know what phishing scams are, common things to look out for, and how to protect yourself from them. Let’s get into it!
What is Phishing?
To put it simply, phishing is “a common type of cyber attack that targets individuals through email, text messages, phone calls, and other forms of communication.” What makes it different from normal communication is that it uses deception in an attempt to access personal information such as bank account information, passwords, credit card information, or other business or personal sensitive information.
Common Types of Scams and Tactics
While we wish we could tell you that phishing is one size fits all, it’s not. There are many types of phishing scams, but once you learn common tricks and tactics, spotting the scams becomes easier. Let’s dig into three common types of phishing scams and things to look out for to avoid them.
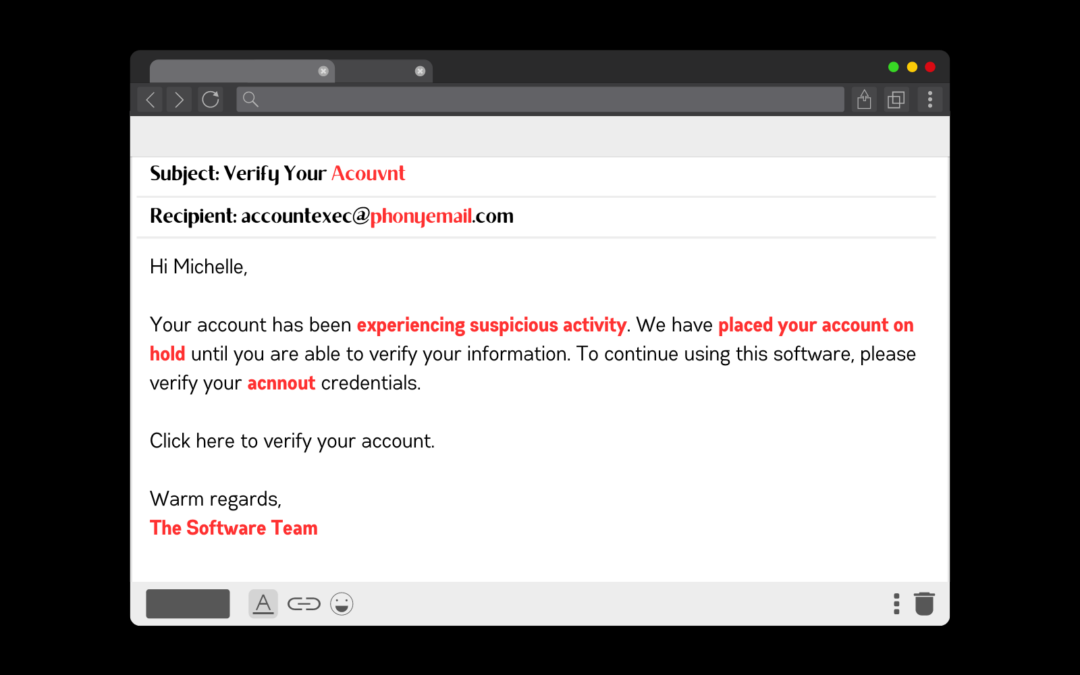
Spear Phishing
These attacks prioritize the quality of the content, and tend to be more sophisticated in nature. They don’t contain as many obvious mistakes as a generic phishing email or scam would. Scammers tend to do more research before sending a spear phishing email, so they may use common phrases used in your company, and the messaging will feel highly personalized to you. A few things to look out for in spear phishing correspondence are:
- Incorrect email addresses
- Embedded URLs (pro tip: hover your cursor over the link to see where it’ll take you before you click…and unless you know for sure it’s from someone you know, don’t click!)
- Slight language discrepancies
Whaling
Whaling attempts target C-suite executives (CEOs, CFOs, CCOs, etc). These attacks look similar to spear phishing, but are used to obtain higher-level, most likely confidential, information. Some things to look out for in whaling correspondence are:
- Generic or incorrect email addresses
- A sense of urgency in the email content
- What type of greeting or closing the impersonator is using—is it typical to what you would see from the person they’re impersonating, or does it feel off?
Any requests for financial information. If you’re unsure whether or not it’s a scam, confirm financial requests with the sender verbally—at least by phone, if not in person.
Voice Phishing
Otherwise known as “vishing”, voice phishing is when an attacker calls or leaves a voicemail for a victim in an attempt to gain access to sensitive information such as login credentials, credit card information, or other identity information. However, these phone calls are always unexpected. In 2022, vishing attacks were the second most popular type of data breach, costing organizations an average of $4.1 million in breach expenses. Some things you can be aware of when it comes to vishing scams:
- If someone calls you unexpectedly pretending to be a trusted organization (the bank, the IRS, a doctor’s office, etc).
- If this call sounds automated
- If the caller is asking for personal information without asking you to verify your identity
- If the caller will not provide a publicly verifiable call back number (you can find this out if you hang up and call back).
Don’t Go Phishing
Whether you work for yourself, are an employee at a corporate organization, are a C-Suite executive, or don’t work at all, you are at risk of falling prey to phishing scams. Anyone with an identity and access to technology is at risk! The best things you can do to avoid these scams and stay protected are:
- Educate yourself on common phishing tactics
- Thoroughly read through every email and text message that comes through
- Intently listen to every voice mail that looks suspicious or unfamiliar
- Avoid clicking on unfamiliar links
- Verify any information you’re being given
We live in a technological world, and that means we have to adapt and arm ourselves against technological and cyber crime. Stay vigilant, and don’t get caught in a phishing scam. Remember: the bad guys do it because it works. Don’t be the next victim.